New
Post Summary
Healthcare organizations rely heavily on third-party vendors, but these partnerships come with significant cybersecurity risks. In 2023, over 133 million health records were exposed, and breaches involving third parties surged by 49% in 2024. The financial impact? A staggering $9.77 million per breach on average for healthcare organizations. Without a structured Third-Party Risk Management (TPRM) program, organizations face data breaches, patient safety risks, and regulatory penalties.
Key Takeaways:
- Third-Party Risks in Healthcare: Vendors like EHR providers and medical device manufacturers can be weak links in cybersecurity.
- Regulatory Requirements: HIPAA and HITECH demand rigorous vendor risk assessments and Business Associate Agreements (BAAs).
- Risk Management Framework: Effective TPRM includes vendor tiering, ongoing monitoring, and risk scoring.
- Technology's Role: Tools like TPRM platforms and AI streamline vendor assessments, reducing delays and improving oversight.
Protecting patient data and ensuring compliance requires a proactive approach to managing vendor risks. Read on to learn how to build a resilient TPRM program and reduce third-party vulnerabilities.
Third-Party Risk Management
Building a Healthcare TPRM Framework
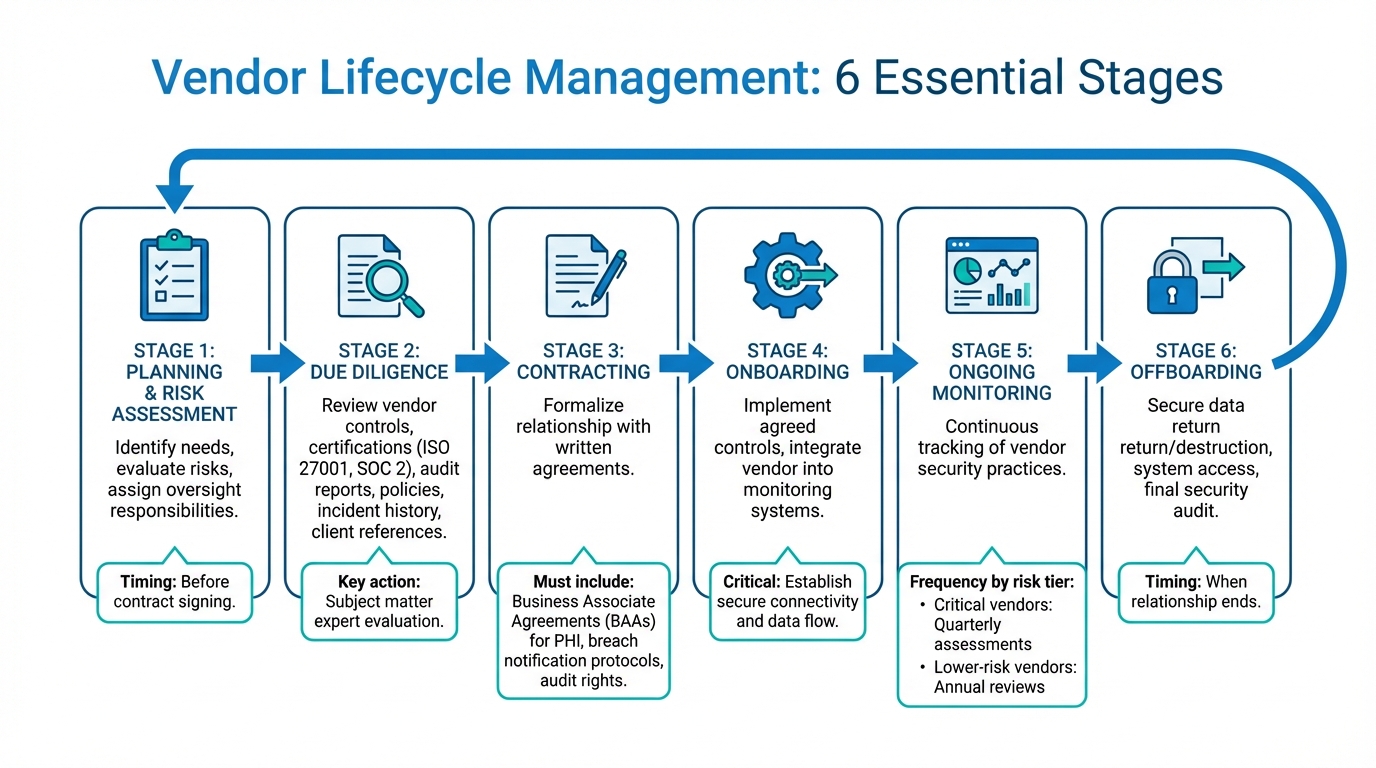
Six Stages of Healthcare Vendor Lifecycle Management
A well-structured Third-Party Risk Management (TPRM) framework simplifies vendor oversight, ensures compliance with HIPAA, and minimizes security threats. Here's how to create a framework that works effectively.
Vendor Lifecycle Management: Main Stages
The vendor lifecycle includes six distinct stages, each designed to safeguard your organization. It begins with planning and risk assessment, where you identify needs, evaluate potential risks, and assign oversight responsibilities before signing a contract. After that comes due diligence. This step involves having subject matter experts review vendor controls, certifications (like ISO 27001 or SOC 2), audit reports, policies, incident history, and client references [1][3].
Next is contracting, where you formalize the relationship through written agreements. These must include Business Associate Agreements (BAAs) for vendors handling Protected Health Information (PHI), as well as breach notification protocols and audit rights [1]. During onboarding, the agreed-upon controls are implemented, and vendors are integrated into your monitoring systems. Ongoing monitoring and reassessment ensures continuous tracking of vendor security practices. The frequency of these reviews depends on the vendor's risk tier - critical vendors might require quarterly assessments, while lower-risk ones may only need annual reviews [1]. Finally, offboarding involves securely returning or destroying data and revoking system access when the relationship ends.
Creating a Central Vendor Inventory
A centralized vendor inventory provides clear visibility into all third-party relationships. This inventory should include vendor names, contact details, contract dates, services provided, data types accessed, system integrations, and assigned risk tiers. It’s essential to go beyond primary vendors and include affiliated organizations, internally-developed software, and clinical trial partners to ensure full oversight [2].
Don’t overlook shadow IT vendors - these are unauthorized third-party tools or services that may have access to your systems. Documenting these vendors helps close security gaps [1]. To make this process easier, consider using TPRM software to store agreements and automate monitoring tasks [1].
Risk Classification and Tiering
Classify vendors based on their risk levels to prioritize oversight where it’s needed most. Vendors can be grouped into four tiers - critical, high, moderate, and low - based on factors like PHI access, operational importance, and regulatory impact [1][3]. For example, critical vendors might include those with direct access to large amounts of PHI, those supporting life-critical medical devices, or those providing essential systems like Electronic Health Records (EHR). High-risk vendors may handle smaller amounts of PHI or support important but non-essential operations. Moderate and low-risk vendors typically offer administrative support or services with minimal data access.
Independent certifications like HITRUST, ISO 27001, or SOC 2 can simplify due diligence [1]. Classify vendors by their PHI exposure, data integration, and use of security measures like Multi-Factor Authentication (MFA) and Single Sign-On (SSO) [2]. Risk tiers also guide how often and how thoroughly vendors are assessed - critical vendors require more frequent and detailed monitoring, ensuring resources are focused on the areas of greatest concern.
Conducting Vendor Risk Assessments
Vendor risk assessments play a crucial role in maintaining a strong Third-Party Risk Management (TPRM) framework. By evaluating external partners thoroughly, you can ensure ongoing oversight and minimize potential risks. After categorizing vendors into risk tiers, dive into detailed assessments to get a clear understanding of their security measures and compliance status. These evaluations should cover both technical safeguards and adherence to regulations, giving you a well-rounded view of the risks each vendor brings to the table.
Information Security Risk Assessments
When assessing a vendor's technical controls, focus on key areas like multi-factor authentication (MFA), encryption protocols (both at rest and in transit), timely vulnerability patching, and the presence of a defined incident response plan. Request documented response plans that outline notification and recovery timelines in case of a breach.
Leverage tools like SIG (Standardized Information Gathering) or CAIQ (Consensus Assessments Initiative Questionnaire) to evaluate their security posture. However, don’t rely solely on self-reported data - ask for external validations such as SOC 2, ISO 27001, or HITRUST certifications. For vendors deemed critical, you might also consider conducting external security scans to uncover vulnerabilities in their public-facing systems.
Compliance Risk Assessments
Ensure the vendor has an updated Business Associate Agreement (BAA) in place. Investigate their history with regulatory compliance, including any violations and the corrective actions taken. Go beyond HIPAA by examining compliance with other relevant regulations, such as FDA guidelines for medical device vendors, state-specific privacy laws, or industry-specific rules like the Anti-Kickback Statute and Stark Law for vendors in referral arrangements [4].
Request audit results, certifications, and documentation of their compliance programs. Also, verify that they conduct regular employee training on privacy and data protection. These compliance insights feed into a structured risk quantification process, helping you assess the overall threat level.
Risk Scoring and Reporting
Combine technical and compliance evaluations to create a standardized risk score. Many organizations use a 5x5 matrix, where risk is calculated by multiplying the likelihood of a security event by its impact. Scores typically fall into these categories:
- Low (1–7): Standard monitoring with annual reviews.
- Moderate (8–13): Periodic audits and specific contractual safeguards.
- High (14–21): Rigorous scrutiny and remediation plans before onboarding.
- Extremely High (22–25): Immediate mitigation or disqualification [4].
Reports should clearly communicate risk levels to decision-makers. Include compliance metrics like HIPAA adherence rates, the number and severity of audit violations, and progress on corrective actions. For IT and SaaS vendors, track metrics such as system uptime, patching delays, and incident response times [4]. Use a Plan of Action and Milestones (POA&M) to document and monitor remediation efforts, ensuring identified risks are actively addressed rather than overlooked [5]. These reports help prioritize vendors requiring immediate attention and highlight the most effective steps to reduce overall risk within your TPRM program.
Managing and Reducing Identified Vendor Risks
Once vendor risks are categorized, the next step is to bring those risks down to acceptable levels. It's essential to prioritize vendors critical to patient safety and revenue, ensuring efforts are directed where they matter most.
Developing Risk Reduction Plans
Using risk scoring as a foundation, craft specific remediation plans. A Plan of Action and Milestones (POA&M) can help track progress. This document should outline tasks, assign responsibilities, allocate resources, and set clear deadlines [5]. For vendors managing electronic health records (EHR), enforce measures like Zero Trust architecture and multi-factor authentication (MFA) to protect sensitive information [4]. These steps reduce the potential for supply chain breaches and limit damage even if credentials are compromised.
Vendors should also be integrated into your broader cybersecurity efforts, including incident response, disaster recovery, and continuity plans [5]. This ensures they understand their role during emergencies and can act effectively. Standardize evaluations with detailed policies and thresholds - vendors in the same risk category should undergo identical audits and mitigation steps [4]. Don’t overlook subcontractors; extend reviews to include these "fourth-party" risks [4].
Remediation and Escalation Processes
When vendors fail to meet security standards, establish clear workflows to address vulnerabilities. Focus on high-risk issues first - these require immediate attention - while moderate risks can follow a scheduled timeline. Always verify remediation with documented evidence of changes in the vendor's security practices to confirm the risk level has genuinely decreased [7].
For unresolved risks, escalate the matter to senior leadership or legal teams. Use "if-then" clauses in Business Associate Agreements (BAAs) to assign accountability for security failures and outline consequences [5]. These contractual terms can help enforce compliance when vendors resist necessary changes. If the partnership ends, use a formal offboarding checklist to revoke access, verify data destruction, and conduct a final security audit [5][4]. This ensures no lingering vulnerabilities from forgotten permissions or data.
Once remediation is complete, attention shifts to managing any remaining risks.
Managing Residual Risks
Even after mitigation, some risks will persist. This is known as residual risk - the level of exposure that remains after all controls are applied. To measure it accurately, start by determining the "inherent risk", which reflects the risk level before any controls were implemented [6]. The difference between inherent and residual risk shows how effective your mitigation efforts have been. It's crucial to document these residual risks and present them to leadership for review and approval, ensuring they align with the organization's overall risk tolerance.
"Residual risk can never be eliminated, but it can be brought to a level that the organization deems acceptable." - Mitratech Staff [8]
Defining your organization's risk appetite in advance helps streamline decision-making [8]. Residual risks should be monitored continuously, using tools to track cyber events like breach notifications, leaked credentials, and dark web activity, as well as business changes like financial instability or leadership turnover [9][11]. Since only 34% of organizations trust their vendors to report breaches promptly [10], independent monitoring is critical. If residual risk surpasses acceptable limits, consider revisiting the vendor relationship or implementing additional controls to address the gap.
sbb-itb-535baee
Using Technology for Scalable TPRM Programs
Handling risk management manually - using spreadsheets and email exchanges - can stretch healthcare risk assessments to a lengthy 45–60 days, leaving organizations vulnerable to rapidly evolving threats [13]. This inefficiency highlights the need for digital tools that can scale with growing demands.
Limitations of Manual TPRM Processes
Manual processes like spreadsheets and email workflows come with more than just delays. Tracking hundreds of vendors manually increases the likelihood of human error, leading to missed deadlines, incomplete assessments, and inconsistent risk evaluations [12]. As vendor networks expand, these inefficiencies multiply, making it nearly impossible to scale without adding more personnel.
Key Features of Healthcare-Specific TPRM Platforms
Platforms like Censinet RiskOps™ address these challenges by acting as a centralized hub for managing risk assessments. They track assessment statuses, risk scores, and remediation progress in real time, eliminating the need for endless email chains. Automated workflows streamline the process by sending questionnaires directly to vendors and issuing reminders for overdue responses. By standardizing assessments across vendors in the same risk tier, these platforms ensure consistent evaluations while reducing reliance on subjective judgment. Additionally, built-in monitoring keeps tabs on vendor security postures, flagging new vulnerabilities as they arise. This creates a "flywheel" effect - each completed assessment improves the system’s efficiency, speeding up future evaluations and reducing risks [13].
The Role of AI in TPRM
Censinet AI™ takes automation a step further, cutting reassessment times to less than a day on average [14]. AI tools allow vendors to complete security questionnaires in seconds by analyzing past responses and auto-filling documented controls. The platform also summarizes vendor evidence and documentation, pulling out key details about product integrations and fourth-party risks. Over time, it builds a comprehensive risk history that tracks remediation efforts and changes, ensuring an audit-ready record for regulatory reviews and investigations. Importantly, human oversight remains a critical part of the process - teams configure rules and validate AI findings to maintain control over decision-making. [14].
Measuring and Improving TPRM Program Performance
Tracking the right metrics is what sets apart a reactive third-party risk management (TPRM) program from one that's strategic. Healthcare organizations should focus on four core categories for performance measurement: Risk (criticality and assessment status), Threat (intelligence and active indicators), Compliance (adherence to regulations like HIPAA), and Coverage (the percentage of the supply chain actively managed) [16]. Without these metrics, risk teams often struggle to demonstrate their value to leadership or identify bottlenecks that could leave the organization vulnerable. These measurements are the foundation for effectively evaluating vendor performance.
Key Performance Indicators for TPRM Programs
Some key performance indicators (KPIs) to track include:
- Average time to complete vendor assessments
- Proportion of vendors with completed inherent risk evaluations
- Percentage of vendors subject to HIPAA or GDPR controls
Another critical metric is Mean Time to Onboard (MTTO), which measures how quickly vendors move from initial engagement to being fully operational. When presenting these metrics to leadership, it’s essential to translate them into financial terms and illustrate how they impact the organization’s overall risk exposure [16].
Using Maturity Models to Assess Program Development
Maturity models act as a guide to help organizations move from basic, reactive processes to more strategic and optimized TPRM programs. Here’s a breakdown of the levels:
- Level 1 (Immature): Relies on manual spreadsheets and undocumented practices.
- Level 2 (Developing): Introduces standardized questionnaires but remains largely manual.
- Level 3 (Scalable): Breaks down silos, enabling collaboration between IT security, procurement, and legal teams through semi-automated platforms.
- Level 4 (Optimized): Employs automated workflows and focuses on data-driven, continuous improvements.
- Level 5 (Visionary): Fully automates processes, anticipates risks, and fosters proactive collaboration with vendors to reduce shared exposure [15].
To advance through these levels, organizations need to invest in technology, create standardized procedures, define roles clearly, and use weighted scoring systems to minimize subjective decision-making [15]. These maturity insights align with earlier discussions on scalable risk management and highlight the importance of continuous improvement.
Benchmarking Against Industry Standards
Internal metrics are just one piece of the puzzle. To get a full picture, benchmark your TPRM program against established frameworks like the NIST Cybersecurity Framework or HITRUST. This process helps identify gaps in your program, ensuring vendors are categorized correctly. For example, over-scrutinizing low-risk vendors can waste resources, while under-evaluating critical ones increases exposure.
Consider this: 41% of companies reported experiencing a significant third-party data breach within a 12-month period [15]. Regular benchmarking keeps your program ahead of emerging threats, allowing you to adapt proactively rather than reacting after an incident.
Conclusion: Strengthening Healthcare Cybersecurity Through TPRM
Third-party risk management (TPRM) isn't just about safeguarding data - it’s about protecting lives. When vendors handling sensitive information like protected health information (PHI) face breaches or disruptions, the ripple effects can be severe. A 2022 Ponemon Institute report revealed that ransomware attacks in healthcare were linked to increased patient mortality rates and longer hospital stays [18]. As Censinet aptly states, "Cybersecurity isn't just about protecting data, it's about protecting people's lives" [18].
Traditional manual methods struggle to keep pace with the ever-changing threat landscape. To stay ahead, healthcare organizations need centralized vendor inventories, risk-based assessments, and continuous monitoring. Regulatory requirements further demand rigorous oversight, which can quickly become unmanageable without the right tools [1]. Adopting digital solutions is no longer optional - it’s essential for building a proactive and resilient cybersecurity framework.
Censinet RiskOps™ tackles these challenges head-on with its Digital Risk Catalog™, featuring over 40,000 pre-assessed vendors and products. This eliminates the need for repetitive initial evaluations [14]. The platform also uses delta-based reassessments, cutting reassessment times to less than a day compared to the 45–60 days required by traditional processes [17]. Tools like automated Corrective Action Plans (CAPs) and 1-Click sharing streamline the process even further, enabling vendors to share security information with multiple healthcare organizations efficiently while maintaining transparency [14].
Censinet AI™ adds another layer of efficiency by seamlessly integrating into risk management workflows. It accelerates tasks like completing questionnaires, summarizing evidence, and generating risk reports - all while ensuring human oversight remains central. This "human-in-the-loop" approach ensures that automation supports critical decisions rather than replacing them, keeping patient safety at the forefront.
A strong TPRM program, backed by technology tailored to healthcare, is key to building resilience against cyber threats. With such systems in place, organizations can safeguard patient data, meet regulatory demands, and maintain operational stability even when third-party incidents arise. This comprehensive approach strengthens both data security and the continuity of care.
FAQs
What are the key stages in managing a healthcare vendor's lifecycle?
The healthcare vendor lifecycle revolves around three key stages: onboarding, ongoing monitoring, and offboarding.
In the onboarding phase, healthcare organizations evaluate vendor risks, confirm compliance, and establish contracts designed to safeguard their systems and sensitive data. The ongoing monitoring stage involves consistently reviewing vendor performance, identifying any emerging risks, and ensuring security and compliance are upheld throughout the partnership. Lastly, offboarding focuses on securely ending the vendor relationship, which includes ensuring data is either returned or destroyed and revoking access to prevent potential breaches.
These steps are crucial for protecting patient information, reducing risks, and staying aligned with regulatory standards.
How does AI enhance Third-Party Risk Management (TPRM) in healthcare?
AI is transforming Third-Party Risk Management (TPRM) in healthcare by streamlining critical processes and delivering real-time insights. One standout feature is continuous monitoring, which keeps a close eye on vendor activities. This means unusual behaviors, vulnerabilities, or compliance issues can be spotted quickly, allowing organizations to tackle risks as they arise. The result? A lower chance of data breaches or disruptions to operations.
Another major advantage is the use of predictive analytics. By analyzing both historical and real-time data, AI can forecast potential risks, helping healthcare organizations focus their attention on high-risk vendors and use their resources more effectively. On top of that, AI simplifies compliance management by automating tasks like regulatory tracking and audits. This ensures adherence to critical standards like HIPAA and HITECH with far less manual effort.
With AI-driven tools, healthcare providers can approach third-party risk management in a way that’s more efficient, precise, and proactive - protecting sensitive data while keeping operations running smoothly.
What essential features should a healthcare TPRM platform have?
When selecting a TPRM (Third-Party Risk Management) platform tailored for healthcare, there are a few key features to prioritize. Look for automation tools designed to streamline risk assessments and workflows. These can save time and reduce manual effort. Additionally, real-time dashboards are essential for providing clear, up-to-the-minute insights into potential risks, helping teams act quickly and confidently.
The platform should also align with industry standards like NIST, HIPAA, and ISO, ensuring compliance while enabling faster and more precise data analysis. This alignment is crucial for maintaining regulatory requirements and managing sensitive information.
Other must-have features include secure data sharing, which encourages smooth collaboration between healthcare providers and their vendors, and continuous monitoring to stay ahead of evolving risks. Finally, actionable remediation tools are vital for addressing issues promptly, minimizing disruptions, and bolstering security. Together, these capabilities help healthcare organizations not only manage third-party risks efficiently but also safeguard critical patient data.
Related Blog Posts
- Common Healthcare Third-Party Risk Assessment Questions
- Third-Party Risk Management vs. Vendor Management: What Healthcare Leaders Need to Know
- Healthcare Third-Party Risk Management Trends 2025: What's Changing and Why It Matters
- Healthcare Third-Party Risk Management Maturity Model: Where Does Your Organization Stand?


