Illinois BIPA vs. HIPAA: Key Differences for Healthcare
Post Summary
The Illinois Biometric Information Privacy Act (BIPA) regulates the collection, use, and storage of biometric data, requiring consent and transparency.
The Health Insurance Portability and Accountability Act (HIPAA) protects patient health information (PHI) and ensures compliance with privacy and security standards.
BIPA focuses on biometric data and allows private lawsuits, while HIPAA governs broader health information and lacks a private right of action.
Yes, but biometric data used for healthcare treatment, payment, or operations under HIPAA may be exempt from BIPA’s requirements.
BIPA requires consent, notice, and data retention policies, while HIPAA mandates safeguards for PHI and regular risk assessments.
Compliance with both laws protects patient data, reduces legal risks, and ensures adherence to privacy standards.
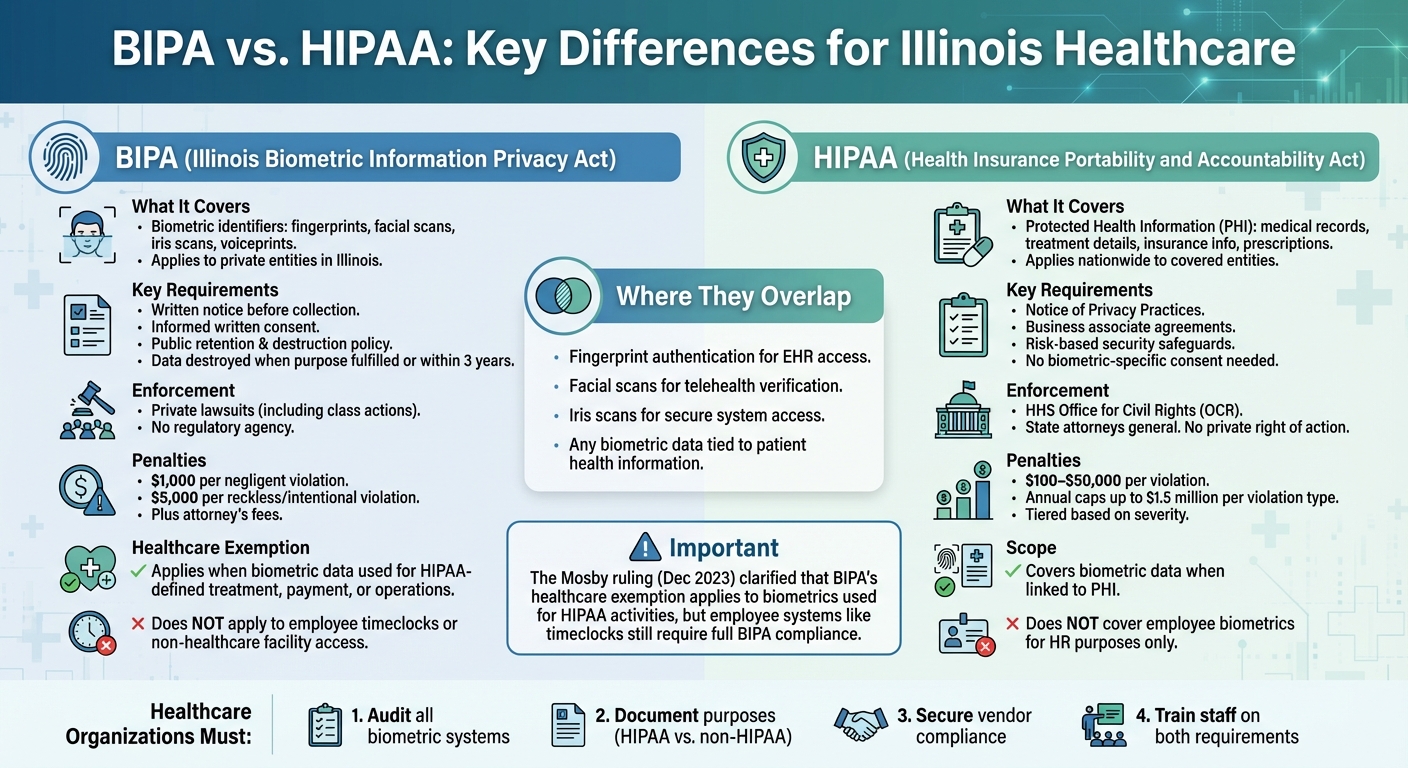
Illinois healthcare organizations face overlapping privacy laws - BIPA and HIPAA - when handling biometric data. Here's the key takeaway: BIPA regulates biometric data collection with strict notice and consent rules, allowing individuals to sue for violations. HIPAA focuses on safeguarding Protected Health Information (PHI) with federal oversight and no private lawsuits.
Quick Overview:
- BIPA: Applies to biometric data like fingerprints and facial scans; mandates written consent and retention policies; steep penalties ($1,000–$5,000 per violation).
- HIPAA: Covers PHI, including biometric data tied to healthcare; requires security safeguards; enforced by federal regulators with fines up to $1.5M per violation type.
- Overlap: Both apply when biometric data is linked to PHI (e.g., fingerprints for EHR access). However, BIPA governs non-healthcare uses like employee time clocks.
Recent Update:
The Mosby ruling (Dec 2023) clarified BIPA's healthcare exemption for HIPAA-related activities like treatment, payment, or operations. But non-HIPAA uses (e.g., employee systems) still fall under BIPA.
Key Action for Providers: Audit biometric systems, document their purposes, secure vendor compliance, and train staff to differentiate between BIPA and HIPAA requirements.
BIPA vs HIPAA Comparison Chart for Healthcare Organizations
Scope of Coverage
To navigate the complexities of managing biometric and health information, it’s essential to understand how the scopes of BIPA and HIPAA differ - and where they overlap.
BIPA's Focus on Biometric Data
The Illinois Biometric Information Privacy Act (BIPA) governs how biometric identifiers are collected, used, stored, and destroyed. This includes data like fingerprints, iris scans, voiceprints, and facial recognition details [1]. The law applies to private entities operating in Illinois that handle biometric data. For instance, a hospital using fingerprint scanners to control medication access or a clinic employing facial recognition for patient check-ins would fall under BIPA regulations unless specific exemptions apply.
HIPAA's Coverage of Protected Health Information
The Health Insurance Portability and Accountability Act (HIPAA) safeguards Protected Health Information (PHI), which includes medical histories, treatment details, lab results, insurance information, and prescription records. Unlike BIPA, HIPAA is a federal law that applies nationwide. It covers healthcare providers, health plans, healthcare clearinghouses, and their business associates. Compliance is enforced by the Office for Civil Rights under the U.S. Department of Health and Human Services, with penalties reaching up to $50,000 per violation [2]. These distinct scopes highlight how healthcare organizations may need to comply with one or both laws depending on the type of data they handle.
Where BIPA and HIPAA Overlap in Healthcare
The two laws intersect when biometric data is tied to health information. For example, a hospital using fingerprint authentication to access electronic health records must comply with both BIPA and HIPAA. Similarly, facial scans for telehealth verification or iris scans for secure system access can trigger obligations under both frameworks. The key difference lies in their requirements: BIPA mandates informed consent for collecting biometric data, while HIPAA focuses on safeguarding the associated health information.
It’s worth noting the Mosby ruling, which exempts biometric data used strictly for treatment or payment from BIPA. However, biometric data used for non-HIPAA purposes - such as employee timekeeping or facility access - remains subject to BIPA. This distinction underscores the need for healthcare organizations to carefully assess how they handle biometric data, depending on its purpose.
Exemptions and Overlaps
BIPA's Healthcare Exemptions
The Illinois Biometric Information Privacy Act (BIPA) includes two specific exemptions for "biometric identifiers." The first exemption applies to data collected from a patient within a healthcare setting. The second covers biometric information gathered, used, or stored for healthcare treatment, payment, or operational purposes, as defined under the Health Insurance Portability and Accountability Act (HIPAA).
On November 30, 2023, the Illinois Supreme Court addressed these exemptions in Mosby v. Ingalls Memorial Hospital. The Court clarified that HIPAA's exemption extends to both patient and employee biometric data when used for treatment, payment, or operational activities. In this case, nurses used fingerprint scans to access medication and medical supplies for patient care. The Court unanimously ruled that this activity fell under BIPA's HIPAA exemption.
However, the exemption has clear limits. It does not provide blanket coverage for all biometric systems used in healthcare. For example, employee fingerprint time clocks used solely for tracking attendance do not align with HIPAA-defined activities and remain subject to BIPA. Similarly, facial recognition systems for building access or cafeteria payments are unlikely to qualify under the exemption. These distinctions highlight the importance of evaluating each biometric use case to determine whether it aligns with HIPAA's scope. This ruling underscores the nuanced relationship between HIPAA and BIPA's requirements.
HIPAA Preemption of State Laws
While BIPA carves out specific exemptions, HIPAA operates as a broader federal standard. However, HIPAA allows for stricter state privacy laws, such as BIPA, to take precedence. Unlike HIPAA, BIPA requires written notice and consent, enforces data retention and destruction policies, and permits private lawsuits - none of which are explicitly mandated by HIPAA.
HIPAA provides the baseline for protecting health information, but BIPA imposes additional obligations for biometric data in Illinois. For instance, if a hospital uses facial recognition for marketing purposes or general security - functions that do not involve protected health information (PHI) under HIPAA - then HIPAA does not preempt BIPA. In such cases, healthcare organizations must comply with both frameworks. This means that simply adhering to HIPAA standards is not enough to meet Illinois' stricter biometric privacy rules.
Comparison Table: BIPA Exemptions vs. HIPAA Definitions
| BIPA Exemption | HIPAA Definition | Example |
|---|---|---|
| Data collected from a patient in a healthcare setting | HIPAA does not specifically define "patient" or "setting" | Fingerprint scans used in a clinical optometry practice |
| Data gathered for treatment, payment, or operations under HIPAA | Covers provider activities like care delivery, billing, and quality audits | Nurse fingerprints used to access medication for patient care |
| Excludes employee biometrics unrelated to HIPAA purposes | HIPAA focuses on patient PHI, not employee biometric data | Fingerprints for employee time clocks (subject to BIPA rules) |
Compliance Requirements and Penalties
BIPA's Notice and Consent Requirements
Under BIPA, organizations are required to publicly share a written policy that explains how biometric data is retained and when it will be destroyed. Before collecting any biometric data, they must provide written notice that clearly outlines what data is being collected, why it’s being collected, and how long it will be kept. Additionally, separate written consent is required for each specific use of the biometric data.
For hospitals, this means obtaining standalone consent for biometric data, rather than including it within broader HIPAA or employment-related forms. Each use - whether it’s fingerprint access to medication cabinets, facial recognition for patient check-ins, or employee time tracking - must have its own explicit consent documentation. Common missteps include vague retention timelines or assuming that HIPAA consent automatically covers biometric data, which it does not.
One of the most challenging aspects of BIPA is its private right of action, which allows individuals to file lawsuits even if they haven’t experienced actual harm. Violations come with steep penalties: $1,000 for each negligent violation and $5,000 for reckless or intentional violations, plus the possibility of attorney’s fees and court orders. Since each biometric scan or day of noncompliance can be treated as a separate violation, class-action lawsuits have exposed healthcare providers in Illinois to potential liabilities reaching tens or even hundreds of millions of dollars. This has led some organizations to pause or completely rework their biometric programs to avoid these risks.
In comparison, HIPAA takes a different approach to enforcement and safeguards, as outlined below.
HIPAA's Privacy and Security Rules
Unlike BIPA, HIPAA focuses on broader privacy and security measures rather than specific consent for biometric data. Under HIPAA, organizations must provide a Notice of Privacy Practices, sign business associate agreements, and implement safeguards based on risk assessments. Separate consent for biometric data isn’t required, as the Privacy Rule allows covered entities to use and share Protected Health Information (PHI) for treatment, payment, and healthcare operations without additional written authorization.
HIPAA’s Security Rule mandates a comprehensive approach to protecting data. For biometric systems, this includes restricting access to biometric templates, logging all system activity, encrypting data both at rest and in transit, and ensuring third-party vendors adhere to equivalent security standards.
Enforcement of HIPAA falls under the U.S. Department of Health and Human Services Office for Civil Rights (HHS/OCR), with occasional involvement from the Department of Justice. Unlike BIPA, HIPAA does not grant individuals the right to sue directly. Instead, penalties are imposed by regulators and follow a tiered structure based on the severity of the violation. These range from $100 to $50,000 per violation, with annual caps as high as $1.5 million per violation type, adjusted periodically for inflation. To address systemic issues, OCR often uses Resolution Agreements and Corrective Action Plans, focusing on areas like inadequate risk assessments, poor access controls, and lack of vendor oversight. These issues are particularly relevant for healthcare providers using biometric systems integrated with electronic health records (EHRs) or access control systems.
Healthcare organizations juggling these complex compliance demands can use tools like Censinet RiskOps™ to streamline third-party risk assessments and monitor vendor security across systems that handle both biometric data and PHI.
Comparison Table: Compliance and Penalties
| Requirement | BIPA | HIPAA |
|---|---|---|
| Notice & Consent | Written notice and informed consent required before collecting biometric data; must specify purpose and duration | Notice of Privacy Practices required for PHI; separate authorization needed for uses outside treatment, payment, and operations; no biometric-specific consent required |
| Policies & Retention | Publicly available retention and destruction policy with specific timelines (data destroyed when purpose is fulfilled or within three years of last interaction) | Policies and procedures required; documentation retention generally six years; no specific destruction timelines for PHI; requires secure disposal and "minimum necessary" use |
| Security Safeguards | Reasonable safeguards, at least as protective as those for other confidential information | Administrative, physical, and technical safeguards based on risk analysis, including encryption, access controls, and workforce training |
| Enforcement Body | Private lawsuits (including class actions) in Illinois state and federal courts | HHS Office for Civil Rights (OCR) and state attorneys general; no private right of action |
| Penalties | $1,000 per negligent violation; $5,000 per reckless or intentional violation; includes injunctive relief and attorney’s fees | $100–$50,000 per violation depending on severity; annual caps up to $1.5 million per violation type (adjusted for inflation) |
sbb-itb-535baee
How Healthcare Organizations Can Comply with Both Laws
Dual Compliance Challenges
Healthcare organizations in Illinois face a unique challenge when navigating BIPA (Biometric Information Privacy Act) and HIPAA (Health Insurance Portability and Accountability Act). These two laws operate independently, meaning compliance with one doesn’t automatically satisfy the other. The real complexity lies in determining which biometric uses fall under BIPA, which qualify for BIPA's narrow healthcare exception, and which require adherence to both laws simultaneously.
Take this example: a nurse using fingerprint authentication to access a Pyxis medication cabinet for patient care. In this case, the biometric data qualifies for BIPA's healthcare exception because it supports HIPAA-related treatment. Contrast that with the same nurse using a fingerprint timeclock for employee check-ins. This use is fully subject to BIPA's requirements for notice, consent, and data retention, but it falls outside HIPAA since it’s solely an HR function. This kind of fragmentation demands clear, detailed policies to ensure staff know when and how each regulation applies.
The challenge grows when biometric systems are deployed across multiple use cases. For instance, a facial recognition system might be used for patient check-ins, where it involves PHI (protected health information) and triggers HIPAA's Security Rule. The same system used for employee building access, however, is not covered by HIPAA but must meet all BIPA requirements. This dual application forces organizations to maintain separate documentation, consent processes, and technical safeguards for each scenario, adding to administrative and training burdens. To handle this effectively, organizations need to implement systematic risk management strategies.
Risk Mitigation Strategies
To address these challenges, healthcare organizations should start with a comprehensive inventory of all biometric systems. This includes everything from medication cabinets and EHR access to timeclocks, facility access systems, telehealth platforms, and patient kiosks. For each system, document whose data is being collected (patients or employees), the purpose of the data, and whether it supports HIPAA functions like treatment, payment, or operations. This mapping exercise helps pinpoint high-risk uses that demand stricter BIPA compliance.
Another key step is strengthening vendor contracts. Biometric system vendors must commit to BIPA-compliant practices, including strict controls on data sale, disclosure, retention, and responding to subject requests. At the same time, vendors handling PHI must meet HIPAA's requirements for security and breach notifications. Many healthcare organizations use integrated risk management platforms to streamline vendor assessments. For example, Censinet RiskOps™ is specifically designed for healthcare organizations, enabling efficient third-party risk assessments and collaborative management of systems that handle both PHI and biometric data.
From a governance perspective, it’s crucial to involve compliance, privacy, HR, and IT security teams in overseeing biometric risks. Regular training should be conducted to clarify when BIPA applies, how it differs from HIPAA, and the steps to take if a biometric system is compromised. High-risk, high-volume uses - like employee timeclocks and access control systems - should be prioritized for remediation, as they carry the highest potential exposure under BIPA. Embedding these practices into daily operations is essential for managing dual compliance effectively.
Comparison Table: BIPA vs. HIPAA Compliance Trade-offs
| Factor | BIPA | HIPAA |
|---|---|---|
| Litigation Risk | High - private right of action with $1,000–$5,000 statutory damages per violation; potential for class actions | Low - no private right of action; enforcement through HHS OCR and state attorneys general with tiered penalties |
| Scope Limitations | Narrow healthcare exception applies only to biometrics supporting HIPAA-defined treatment, payment, or operations (e.g., medication cabinet access); most employee and facility uses fall under BIPA | Covers all PHI, including biometric data linked to identifiable individuals; excludes employee biometrics used solely for HR or security |
| Enforcement Bodies | Illinois state and federal courts via private lawsuits and class actions; no regulatory agency oversight | HHS Office for Civil Rights (OCR), state attorneys general; enforcement through investigations, corrective actions, and agreements |
| Compliance Flexibility | Rigid - requires explicit written notice, consent, public retention policies, and specific data destruction timelines | Risk-based - allows safeguards tailored to the organization’s size, complexity, and risks, with policies updated as needed |
| Vendor Management | Requires BIPA-specific contract terms (e.g., indemnification, compliance commitments) for all biometric vendors, regardless of PHI involvement | Business associate agreements required only for vendors handling PHI, with terms aligned to the Security Rule |
Conclusion
Key Takeaways
Healthcare organizations in Illinois must juggle compliance with two distinct laws: BIPA and HIPAA. While both address data protection, their focus and enforcement mechanisms differ significantly. BIPA emphasizes written consent and notice for biometric data, allowing individuals to sue directly for violations, which can lead to costly class action lawsuits. In contrast, HIPAA focuses on safeguarding protected health information (PHI) through federal oversight. A major distinction is that BIPA's direct legal recourse makes it a more immediate risk for organizations.
BIPA does offer a healthcare exemption, but only for biometric data used in activities defined under HIPAA, as clarified in the Mosby v. Ingalls Memorial Hospital case. However, this exemption doesn’t extend to employee-related uses, such as biometric timeclocks, which remain fully subject to BIPA. This dual compliance challenge means organizations must implement separate policies for systems that serve both patient care and employee management, adding layers of complexity and increasing the risk of litigation.
Recommendations for Healthcare Organizations
To navigate these challenges, healthcare organizations should adopt a structured, proactive approach to compliance:
- Audit Biometric Systems: Start with a thorough review of all biometric systems. Document the type of data collected, its purpose, and whether it ties to HIPAA-defined activities. This will help pinpoint high-risk areas requiring strict BIPA compliance and clarify where exemptions might apply.
-
Strengthen Vendor Contracts: Work closely with biometric vendors to ensure contracts include BIPA-specific terms. These should cover data handling, retention, and destruction practices. If vendors also handle PHI, make sure business associate agreements align with HIPAA's security and breach notification requirements. Tools like Censinet RiskOps™ can simplify third-party risk assessments, especially for systems managing both PHI and biometric data. Matt Christensen, Sr. Director of GRC at Intermountain Health, emphasizes the unique challenges in this space:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." [3]
- Establish Cross-Functional Governance: Bring together compliance, privacy, HR, and IT security teams to create a unified strategy. Regular training should ensure staff understand when BIPA applies, how it differs from HIPAA, and the steps to follow if a breach occurs. Focus on high-risk systems like employee timeclocks and access controls, as these are common sources of BIPA violations.
FAQs
What are the biggest compliance challenges for healthcare organizations under BIPA and HIPAA?
Healthcare organizations face a tough road when it comes to staying compliant with BIPA and HIPAA, as each comes with its own set of rules.
BIPA zeroes in on biometric data - things like fingerprints or facial scans. It demands that organizations get explicit consent from individuals, store this data securely, and delete it in a timely manner. Falling short here can lead to legal trouble and expensive lawsuits.
HIPAA, meanwhile, focuses on protecting patient health information (PHI). It sets strict privacy standards, requires robust security measures, and mandates clear protocols for notifying individuals in the event of a data breach.
To stay on the right side of both laws, healthcare organizations need to establish clear policies, regularly assess risks, and keep a close eye on compliance through continuous monitoring.
What impact does the Mosby ruling have on how BIPA applies to healthcare organizations?
The Mosby ruling has refined how Illinois’ Biometric Information Privacy Act (BIPA) applies within the healthcare sector. Specifically, it limits the scope by excluding certain government functions and placing the primary focus on private entities. As a result, healthcare organizations are less likely to encounter BIPA-related claims if their activities fall under these outlined exceptions.
For healthcare providers, this decision alleviates some of the compliance challenges tied to managing biometric data. That said, it's still crucial to handle biometric information responsibly. Providers must ensure they meet both BIPA and HIPAA standards to protect patient data and maintain strict privacy safeguards.
How can healthcare providers comply with both BIPA and HIPAA regulations?
To meet the demands of both BIPA and HIPAA, healthcare providers need to implement thorough risk management strategies tailored to the specific requirements of each regulation. This involves steps like encrypting biometric data to protect it from unauthorized access, performing regular audits to identify and address vulnerabilities, and ensuring staff are properly trained to handle sensitive information responsibly.
Leveraging a specialized risk management platform can make compliance more manageable. These tools allow for continuous risk assessments and help streamline workflows. Beyond that, healthcare organizations should establish clear policies for how biometric data is collected, stored, and shared. Consistent monitoring is also essential to ensure ongoing compliance with both regulatory frameworks.
Related Blog Posts
Key Points:
What is Illinois BIPA?
- The Illinois Biometric Information Privacy Act (BIPA) regulates the collection, use, and storage of biometric data, such as fingerprints, retina scans, and facial recognition.
- It requires organizations to obtain informed consent, provide notice about data collection and usage, and establish retention and destruction policies.
- BIPA allows individuals to file private lawsuits for violations, even without proving actual harm.
What is HIPAA?
- The Health Insurance Portability and Accountability Act (HIPAA) protects patient health information (PHI) by setting privacy and security standards for healthcare organizations and their business associates.
- HIPAA governs the use, storage, and sharing of PHI, ensuring confidentiality, integrity, and availability of patient data.
- Unlike BIPA, HIPAA does not allow private lawsuits but enforces compliance through federal oversight and penalties.
How does BIPA differ from HIPAA?
- Scope of Data: BIPA focuses exclusively on biometric data, while HIPAA governs broader categories of health information, including medical records and PHI.
- Private Right of Action: BIPA allows individuals to sue for violations, whereas HIPAA does not provide this option.
- Regulatory Focus: BIPA emphasizes consent and transparency for biometric data, while HIPAA mandates safeguards and risk assessments for PHI.
Does BIPA apply to healthcare organizations?
- Yes, BIPA applies to healthcare organizations, but there are exceptions.
- Biometric data collected, used, or stored for healthcare treatment, payment, or operations under HIPAA may be exempt from BIPA’s requirements.
- For example, biometric data used by healthcare workers to access medication-dispensing systems for patient care is excluded from BIPA.
What are the compliance requirements for BIPA and HIPAA?
- BIPA Compliance:
- Obtain informed consent before collecting biometric data.
- Provide written notice about the purpose and duration of data collection.
- Establish and follow retention and destruction policies.
- HIPAA Compliance:
- Implement administrative, technical, and physical safeguards to protect PHI.
- Conduct regular risk assessments and audits.
- Ensure business associates comply with HIPAA standards.
Why is understanding BIPA and HIPAA important for healthcare?
- Compliance with both laws protects sensitive patient data and reduces legal risks.
- Understanding the interplay between BIPA and HIPAA ensures healthcare organizations can navigate overlapping regulations effectively.
- Adhering to these laws builds trust with patients and stakeholders by demonstrating a commitment to privacy and security.


